15 Mar Data Classification for Information Security
Ransomware, spyware, phishing, password theft – these are all common information security threats facing organizations. But what about the sneakier, unintentional threats?
Every day, your organization’s employees are accessing, altering, sending, and copying/pasting files. Without the right data classification and controls in place 24/7, your information can be exposed to unwanted access.
So, it’s best practice to build a strong framework to put the right data classification and controls in place.
ABOUT DATA CLASSIFICATION
Information governance’s data classification process involves looking at, sifting through, and categorizing an organization’s data. A well-executed process will not only make information much more findable, it will also strengthen the barrier against information security threats by having the right classifications, permissions, and controls in place.
Basically, correctly classifying data can protect your information from accidentally falling into the wrong hands.
There are three standard ways of classifying data:
-
-
- Context-Based Classification relies on indirect indicators to determine the information’s categorization – most commonly its location, creator, and/or application used.
- Content-Based Classification analyzes the actual composition – the content – to determine the categorization. There are several ways to execute this type of classification, but all use some form of algorithms or machine learning. With these automated processes, content is analyzed for specific phrases or word patterns that help identify what it is.
- User-Based Classification is a manual categorization, which is left up to end-user discretion.
-
Your data classification process should leverage all three. The combination of the methods will ultimately depend on your organization’s needs, tools available, and the team designated to execute it.
A well-rounded team should include your records manager, the governance team, and IT security. Your records manager will know what information your organization has and how it’s being used. A governance team will create (or refine) your framework for how that information is categorized. And IT security will be responsible for applying the correct permissions and controls based on each categorization.
While it’s a great effort to build out (or refine) your framework, it’s an essential first step to keeping your information secure.
WHERE TO START: RISK MANAGEMENT FRAMEWORK
The National Institute of Standards and Technology provides a Risk Management Framework that details the ideal Security Life Cycle. While it’s intended for government agencies and highly regulated industries, we highly recommend it as a best practice for all organizations concerned about information security risks.
The importance of data classification for information security comes to light in the very first step and remains key throughout the life cycle.
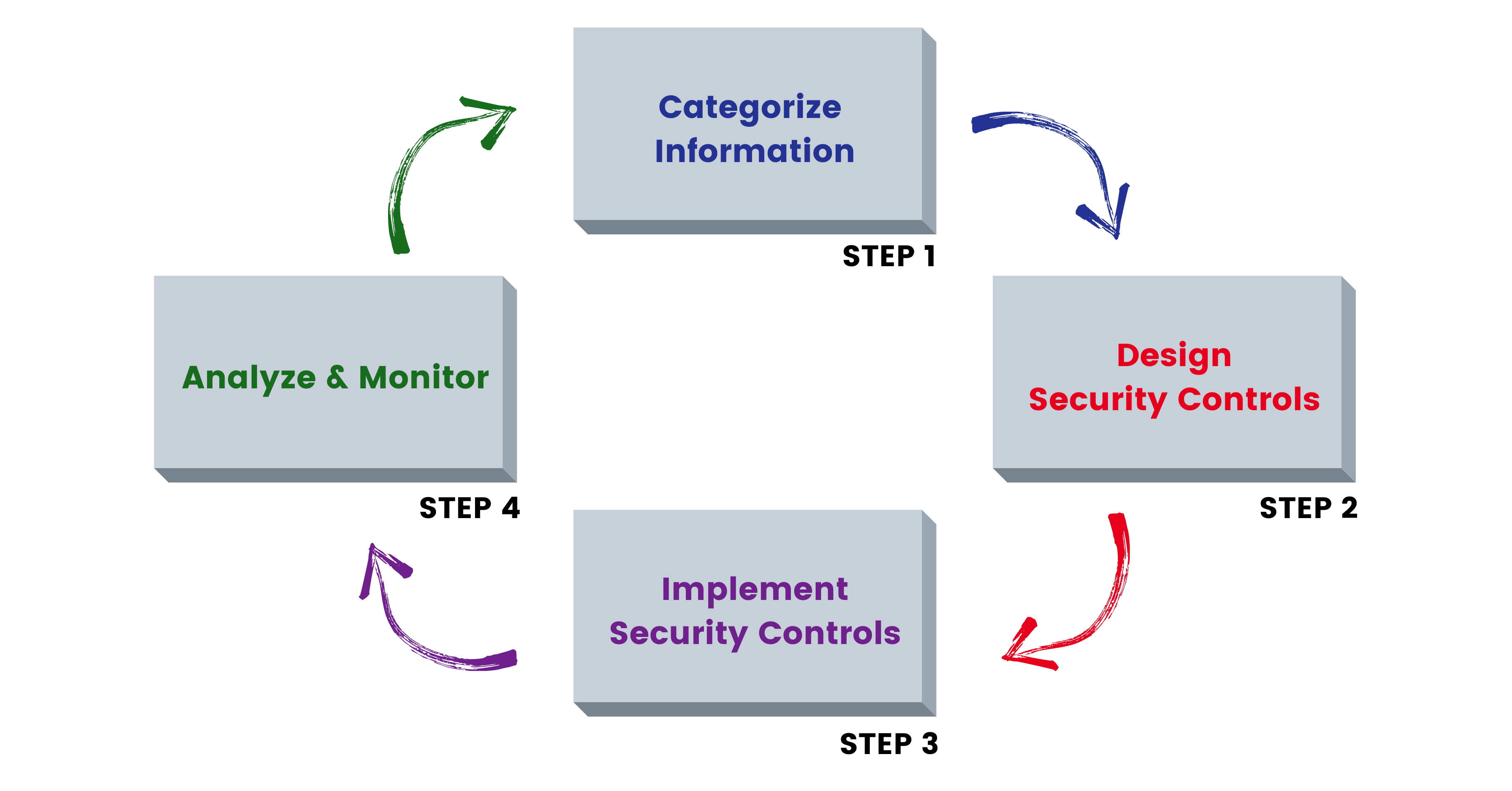
Categorize Information
In this first step, information will be categorized into groups based on the potential business impact – or the consequences – to the organization if the confidentiality, integrity, or availability were to be compromised.
Again, data classification is a team effort. Your records manager and governance team should work together to build out the categories, incorporating data gathering sessions across the organization to determine what information types there are and how they’re being used. This is a long process since there are so many different places information is stored – from on-premises, the Cloud, email, instant messages, and more. Then, they will form categories (for example, Public, Private, and Confidential) based on those information types and their necessary security levels.
Design & Implement Security Controls
In Step 2 and 3, IT security will step in to help the team design and implement the appropriate permissions and controls based on those set categories.
For example, most organizations have employee, customer, and/or client’s Personally Identifiable Information (PII) on file – things like phone numbers, email addresses, and Social Security numbers. While all of these need to be protected, the level of protection applied depends on the classification assigned to it. Your marketing department may need access to customers’ email addresses for promotional messages, but they don’t need access to other employees’ Social Security numbers. However, HR does for Social Security benefits.
So, IT will ensure that only the right people have access to the right information. These steps will prevent information from unintentionally falling into the wrong hands.
Analyze and Monitor
It’s important to note that data classification isn’t a one-and-done effort. The last step will require regular check-ins and potential alterations, especially when your organization experiences a regulation change, a process change, a policy change – or when a new area of business is added.
MORE ON INFORMATION GOVERNANCE
Information governance is much more than just securing your information. It’s the set of policies, roles, responsibilities, and processes that help organizations align with business goals, minimize risk, and ensure compliance of data.
A strong governance plan will:
- Help you achieve business goals.
- Ensure organization-wide consistency.
- Provide the why (in the policies and rules).
- Provide the how (in the processes and procedures).
- Define system controls in place to ensure compliance.
- Include thorough communications and trainings.
- Be adjusted accordingly, based upon measured effectiveness.
FEATURED WEBINAR
If you want to learn more, check out Project Manager Ashely Schilling’s webinar on the 7-point information governance model.