15 Jan Information Security in Microsoft Office 365
When companies made the rapid transition to work-from-home in 2020, information security risks skyrocketed. Offices were shut down suddenly and remote work environments had to be enabled quickly to preserve business continuity. As a result, many individuals (and their companies) were made more vulnerable to cyber-attacks like phishing.
Today – nearly a year later, companies are still facing security risks and threats related to working remotely, making information security a top priority for IT and Information Governance (IG) leaders this year.
So, what can you do to reduce those risks and threats? While additional security measures are highly recommended for optimal protection of your information assets, it’s essential to fully leverage what you already have.
And lucky for Microsoft Office 365 (O365) customers, there are a lot of built-in capabilities readily available to reduce risk in all areas of information security’s CIA Triad: Confidentiality, Integrity, and Availability.
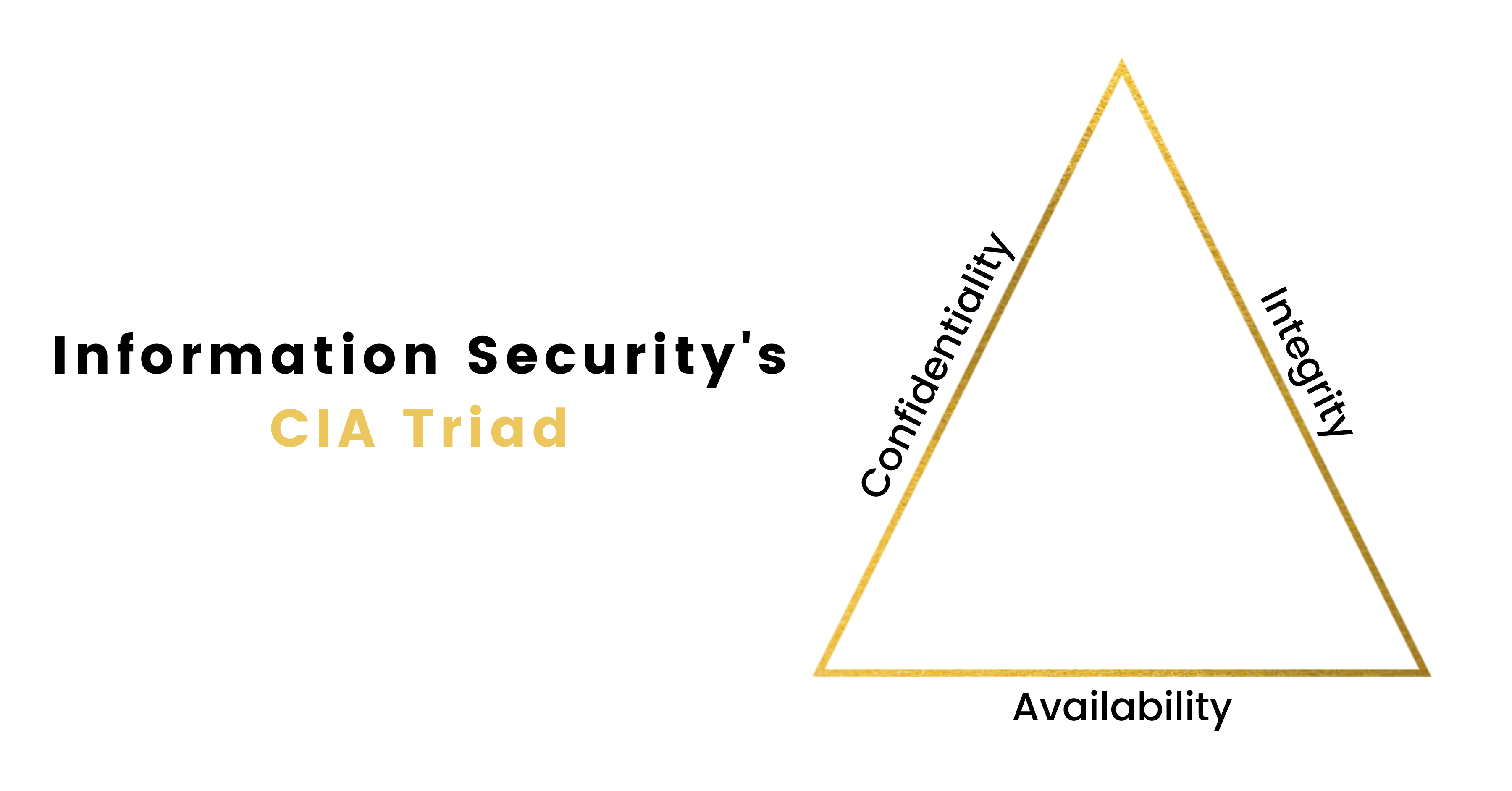
INFORMATION SECURITY & THE CIA TRIAD
The term “information security” refers to the practice of protecting all forms of information – physical and digital – from unauthorized access and modification. The field is guided by the widely accepted CIA Triad, or protecting the Confidentiality, Integrity, and Availability of information.
- If Confidentiality is enabled, only authorized users will be able to access and modify information.
- If Integrity is enabled, information is maintained in its correct state and is guarded from being improperly modified in any way.
- If Availability is enabled, authorized users will be able to access information whenever it’s needed.
Read on to learn how O365’s out-of-the-box (and often underutilized) capabilities meet these three guiding principles to help your organization secure its information assets.
CONFIDENTIALITY
Multi-Factor Authentication adds a second layer of protection and security every time an employee logs in. In addition to the usual username and password, employees will type in a code from an email, phone, or authenticator app to gain access. So, if a hacker successfully gets through the first level of security, the second level will block them from accessing your information.
Here’s a Microsoft resource on how to set up Multi-Factor Authentication: https://support.microsoft.com/en-us/office/secure-employee-accounts-with-mfa-in-microsoft-365-business-e12187b8-216a-4490-9e3b-df34a06fb787?ui=en-US&rs=en-US&ad=US
Data Loss Prevention (DLP) policies, which can be created within the Security & Compliance Center, will identify, monitor, and protect sensitive information throughout your O365. Based on the applied DLP policy, sensitive information (for example, financial data) will be automatically identified and prevented from being shared outside of your organization.
Office Message Encryption keeps email messages confidential when sent to external parties. If the recipient uses a Microsoft email account, they will receive an alert about the message’s restricted permissions. If the recipient uses a non-Microsoft email account, they will either receive a link to sign in or receive a one-time passcode to view the message.
INTEGRITY
Customized Permissions in SharePoint grants organizations the ability to control who can access and alter different libraries, lists, and files while restricting others from doing so. This capability prevents unauthorized users from accidentally or purposefully modifying information housed in SharePoint.
Sensitivity Labels from the Microsoft Information Protection solution let you classify and protect your organization’s data, while making sure that user productivity and their ability to collaborate isn’t hindered. Sensitivity Labels can be used to
- Provide protection settings that include encryption and content markings.
- Protect content in third-party apps and services.
- Protect content in Office apps across different platforms and devices.
AVAILABILITY
Basic Mobility and Security makes accessing O365 on mobile devices safe and secure. It allows your organization to create management policies specific to mobile devices and “wipe” organizational information if the device gets lost or stolen.
Service Resilience, or maintaining service availability (even through system failures), is achieved in O365 through redundant architecture, data replication, and automated integrity checking.
- Redundant Architecture involves deploying multiple instances of a service on physically separate hardware.
- Data Replication involves storing multiple copies of data in different fault-zones. According to Microsoft, this allows data to be recovered if it gets corrupted, lost, or deleted.
- Automated Integrity Checking automatically restores many types of corrupted data.
While these capabilities go a long way to protect your information assets, they barely scratch the surface of all O365 has to offer in terms of information security. To find out if your organization is fully leveraging all its O365 features and how to configure these to meet your specific security needs, contact us to start a conversation with a member of our team.