28 Oct ARMA InfoCon: Advice for Each Stage of Your IG Program
Last week, the Access Sciences team attended ARMA InfoCon 2021 to connect with and learn from other information governance (IG) experts. While we were there, we presented on our own thought leadership and heard a lot of solid advice for building (and sustaining) your IG program.
Following our own 7-Point Governance Model, here are some of our favorite sessions with advice for each stage of your IG program:
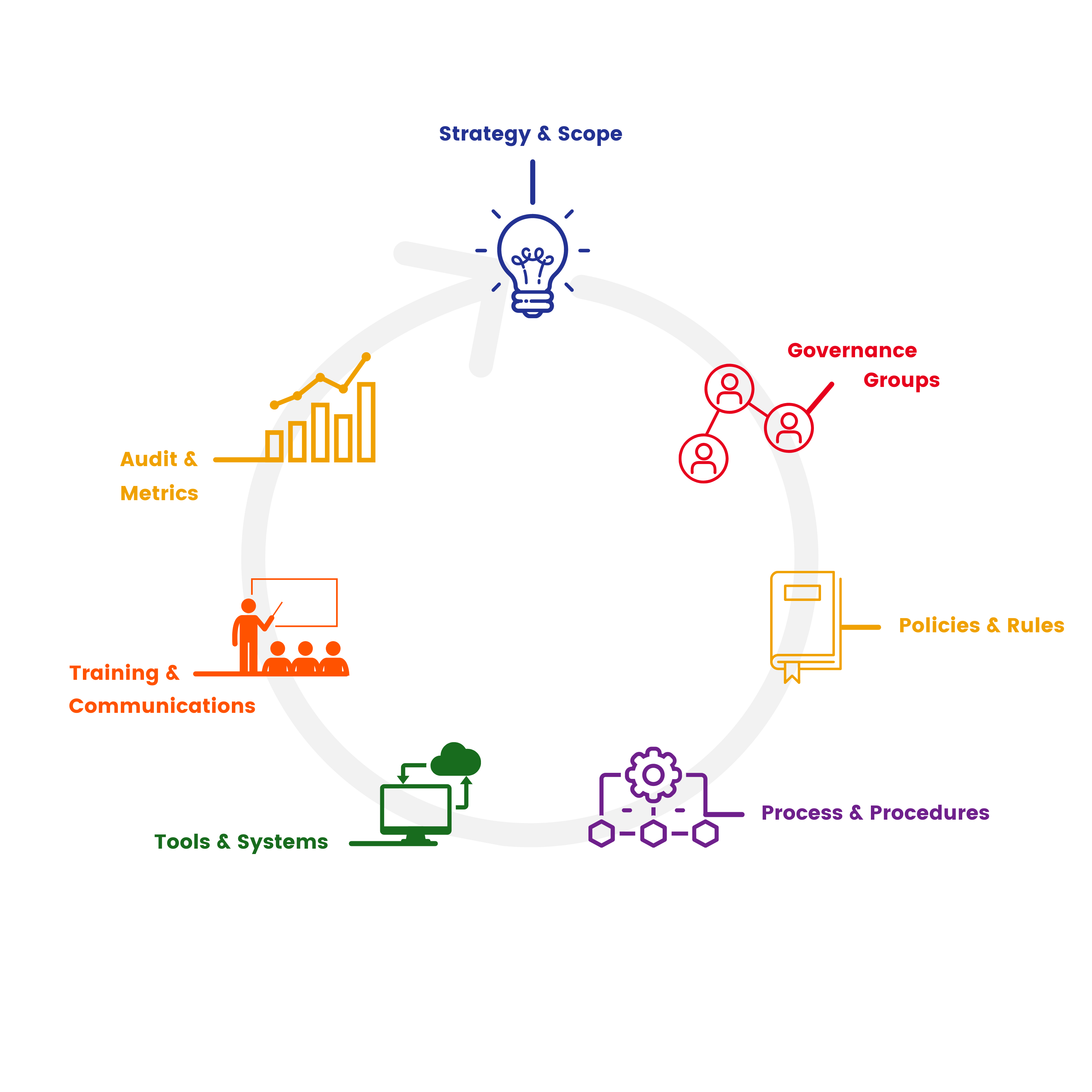
If you missed it, check out our recent blog to learn more about Access Sciences’ 7-Point Governance Model.
STRATEGY & SCOPE
5 Steps to Doing Information Right
Steve Weissman, The Info Guy™, Holly Group
In Step 1: Strategy & Scope, we recommend establishing a vision for your IG program, looking at your available resources, determining your priorities, and focusing on them. Steve Weissman’s ARMA InfoCon session offers advice on how to best execute that with his five steps for building up an IG program.
Step 1: Talk up the benefits.
To start, Steve encourages IG professionals to first answer the question, “Why are we doing this, anyways?” and use that as an opportunity to talk up the benefits of an IG program. He then lists three key benefits to get the conversation started within your organization:
-
-
- It puts your information to work.
-
Your information is there, so you might as well use it and extract value from it.
-
-
- It opens your information up to analysis and insights.
-
This can shorten your time-to-market, identify opportunities for customer upselling, speed up responses to audit requests, and more.
To learn more about IG’s role in information security, check out our blog: “Data Classification for Information Security.”
- It assures your information excellence and security
A strong IG program will minimize information security risk by protecting personally identifiable information, ensuring access by authorized users only, and more.
Step 2: Take Stock (Look Inward)
Similar to our own Governance Model, Steve recommends answering two key questions before embarking on your IG ventures –
1. Where are we now?
2. Where do we want to be?
Step 3: Develop Your Road Map
Once you’ve defined your Point A and Point B, you’ll then want to determine what it’s going to take to get there. To do this, Steve suggests conducting an assessment or gap analysis, which will help you come up with a well-informed game plan towards your desired future state.
To remain strategic when determining your priorities, our team advises organizations to conduct a Records & Information Management (RIM) Assessment to “know what you don’t know” from the very beginning.
For more on assessments, check out our blog: “Assessments: Know What You Don’t Know.”
Step 4: Stay the Course
As with any business feat, you can expect roadblocks ahead. So, commit to the journey!
According to Steve, one of the biggest challenges for IG professionals is getting people on board. That’s why defining the benefits (and communicating them) is essential at the outset of any project.
Step 5: Keep Going (It’s Never Over)
As we like to say at Access Sciences, good governance is never a one-and-done effort. And Steve offers the same exact advice – once your IG program is created, you’ll need to continue analyzing what works and what doesn’t. Then, make changes.
Even after the initial analysis and improvements, Steve recommends conducting a semiannual progress review to make sure your program still fulfills all your information needs.
GOVERNANCE GROUPS
Can’t Get a Seat at the Table? Build Your Own Table!
Earl Johnson, Sr. Records Management Consultant, Cadence Counsel
Step 2: Governance Groups is all about establishing groups across the organization and defining their roles. And we find it’s important that this step starts with gaining executive support.
But what if your organization doesn’t back up your IG initiatives? In his session, Earl Johnson answers that question by describing a time when he (as a Corporate Records Manager) wasn’t invited to the table. So, he made his own.
First, Earl defines what it means to have a seat at the table. He describes “the table” as a symbol of power, negotiation, and credibility which represents the opportunity to be involved in making decisions for your organization.
Then, he offers nine tips to getting a seat at the table:
1. Be confident.
2. Be good at what you do – work proficiency is key.
3. Focus on organizational success.
4. Be gravitational – be someone others like being around.
5. Display strong, authentic, and visionary leadership skills.
6. Listen, and check your ego at the door – listen to understand the issues people are facing.
7. Be patient and work through frustration.
8. Play to your strengths.
9. Be an active participant ready with useful contributions.
While these tips are helpful, they don’t guarantee a seat at the table. So, if you’re constantly blocked from the table, you can build your own. Here are Earl’s tips on how to accomplish this:
1. Define every aspect of the table – what are you trying to accomplish?
2. Get sponsorship from the executive level.
3. Develop a charter.
4. Identify roles and responsibilities – this will differ from organization to organization, but common groups will include IT, legal, and compliance.
5. Recruit, recruit, recruit.
6. Determine targets – identify what you want to address and why.
7. Be a cohesive team.
His own table, which he called the Records Management Advisory Team (RMAT), was made up of a Corporate Records Manager (Earl), two Subject Matter Experts, the Director of Compliance, the Director of Internal Auditing, the Sr. Manager of Operations, the Director of IT, two IT Senior Managers, the VP and General Counsel, and a Sr. Attorney.
According to Earl, the RMAT was successful because the group had the expertise – the right set of individuals to make decisions for the organizations.
POLICIES & RULES
Impact of Data Protection Laws on Your Records Retention Schedule
Tom Corey, Senior Manager, HBR Consulting
In Step 3, IG professionals establish Policies & Rules that balance the need for privacy and security. While this differs significantly based on your company’s culture and regulatory landscape, we’re all facing the current and/or impending impact of data protection laws.
Tom Corey joined ARMA InfoCon to help IG professionals understand data protection laws’ impact on records retention schedules. To start, he defines the key terms:
-
-
- Records Retention Schedule: A policy that (1) identifies the types of records created/retained by the organization and (2) defines the retention period for those identified records.
- Data Protection Laws: Laws and regulations that control the collection, storage, and disclosure of individuals’ personal and sensitive information.
-
According to Tom, the biggest complaint with data privacy laws is that there are so many, and they’re constantly changing. However, he says it’s important to note that these laws are more similar than you think.
Tom explains all data privacy laws and regulations surround Personal Identifiable Information (PII) and retention periods, meaning PII is kept only as long as necessary to fulfill the stated purpose. And to help, he provides four fundamental tools to ensure you stay in compliance with data privacy laws:
1. Retention schedule for all media types
Your retention schedule should reflect your current organization as well as jurisdictions where you operate. It should also reflect the systems in use and be applicable to both paper and electronic records.
2. Identify categories with PII
Tom advises IG professionals to identify marketing and customer information, employee personnel files and job applications, as well as security footage and access information.
3. Justify retention period for those categories
According to Tom, you can justify a retention period with (1) laws and regulations regarding minimum/maximum retention time, (2) a legitimate business purpose (like a contract), or (3) informed consent of the data subject.
4. Add records categories that address data protection laws
Lastly, Tom suggests adding records categories that go along with data protection laws like breach notifications, consumer consents, data subject requests/responses, or privacy policies and procedures.
PROCESS & PROCEDURES
The Real Deal with Autoclassification: Can It Really Be Automatic?
Tom Preece, Director of Pre-Sales Consultancy, North America Rational Enterprise
In Step 4, our experts recommend taking your Policies & Rules and turning them into Processes & Procedures for your organization. In his ARMA InfoCon session, Tom Preece touches on a part of this step by covering auto classification.
With ARMA’s own definition, Tom defined it as “leveraging technologies to automatically analyze information and apply transformation” which can mean –
-
-
- Relocating files
- Adding/removing metadata
- Adding/removing categorization
- Adding/removing policy
- Adding/removing permissions
- Starting a workflow
-
Or “transformation” can mean a combination of all of the above.
Regardless of what you’re trying to do with auto classification, Tom points out that it can’t be leveraged until you define the “if ___, then ___.” For example, if a file reaches the end of its retention period, then it gets deleted.
Before adopting auto classification, Tom recommends asking yourself:
-
-
- What scope of my information can auto classification actually apply to?
- How segmented is my organization? What are their different levels of compliance?
- What are the different formats of my organization’s information?
- What is the quantity of my organization’s information?
- Where is my information?
- How much does it cost me to manually perform the transformation I’m looking to automate?
- What is the cost to implement the technology? Not just quantitative but also qualitative – for example, a negative cultural attitude towards automation.
-
Answers to these questions should be known before making any purchasing decision. Then, you’ll need to determine which approach is right for you – auto-taxonomy, key-value extraction, machine learning? For each of these, you’ll want to prove that it can not only work for day-to-day operations, but that it will also work under the most challenging circumstances your organization faces.
To learn more about LDEQ’s EDMS Redesign, check out our case study and podcast episode for the story behind the project.
TOOLS & SYSTEMS
Streamline Access to Public Records with a Modern EDMS
Glenn Frederickson, Records Management Project Manager, Access Sciences
Tina Gibeson, Senior Records Analyst, Access Sciences
Step 5 is all about choosing Tools & Systems that will support different parts of your data lifecycle. Access Sciences’ experts, Tina Gibeson and Glenn Frederickson, joined ARMA InfoCon to talk about upgrading one of the Louisiana Department of Environmental Quality’s mission-critical systems – its Electronic Document Management System (EDMS).
Traditionally, the public had to go to LDEQ in-person to access records which were stored in file rooms. Then, in 2004, LDEQ hired Access Sciences to develop a public records database that would –
-
-
- Take the records-retrieval burden off LDEQ employees and staff.
- Improve the publics records-retrieval experience.
- Improve information governance.
- Improve legal and compliance.
- Reduce costs.
-
LDEQ’s EDMS officially rolled out in 2006 and has since grown to hold more than 7.25 million documents, host about 5,000 users per month, see about 170,000 page views per month, and experience regional, national, and international access.
However, after 15 years, LDEQ realized its EDMS was starting to show its age. So, LDEQ (along with its now long-term partner, Access Sciences) moved to incorporate new, modern features in five different categories:
1. User Experience
– Updated UI to match LDEQ website design
– Improved process screens to be more intuitive
– Added enhanced visuals
2. Customization & Preferences
– Added an EDMS user account capability for LDEQ staff and public users
– Added a “saved searches” feature
– Added email alert notifications for saved searches
3. Search Enhancements
– Refined searches using faceted-search filters
– Separated quick and advanced search
– Dynamically changed the search layout screen
– Added a toggle between two display types
4. User Authentication
– Built three user levels – LDEQ employee, registered public user, and guest
– Assigned roles and privileges by level
5. Access Restriction and Security
– Assigned tiered document access protection based on user roles – Access Right 1: Public/LDEQ, Access Right 2: LDEQ, and Access Right 5: Authorized LDEQ Only
– Incorporated Captcha for document access
Tina and Glenn’s presentation showed how one system upgrade can change an entire organization, increasing business value significantly. The team uses Google Analytics to track how the EDMS is being used, and the results from the redesign are already proving to justify the cost of the overall records management contract and program.
TRAINING & COMMUNICATIONS
Gaining Buy-In for Your IG Program
Susan Gleason, Information Governance Manager, Shipman & Goodwin LLP
In Step 6: Training & Engagement, we encourage IG professionals to inspire a data-driven culture by training early and communicating often. When it comes to an information-related project, implementing a new system isn’t the hard part – the hard part is getting people to change the way they work.
Change management is often one of the biggest IG roadblocks. That’s why Susan Gleason used her session to offer advice on how to gain buy-in for your IG program. Here are her tips:
-
-
- Always have your elevator speech prepared.
Susan’s first piece of advice to is to prepare an elevator speech for your IG program that is backed by a clear and achievable vision. It should be applicable across the organization, meeting the entire team’s needs – not just yours.
- Always have your elevator speech prepared.
-
- Know your people. Earn their trust.
You should gain an understanding of what people do, how they work, and what they need. Take into consideration different personality types (which Susan describes as the Pioneers, the Guardians, the Drivers, and the Integrators) and what it takes to get each onto your side. Some are more logic-driven (drivers) while some are more relationship-driven (integrators).
- Know your people. Earn their trust.
-
- Follow the KISS Principle.
According to Susan, KISS stands for Keep It Short and Simple. If an IG policy is 30+ pages, make a short, one-page how-to guide for your colleagues. They’ll appreciate the summarized version much more than the original.
- Follow the KISS Principle.
-
- Clarify the reward.
It’s important to communicate the benefits often. What is the organization gaining? What is their specific department or team gaining?
- Clarify the reward.
-
- Make it fun!
Our team likes to use several training and communications methods to reach our different audiences. Send out an information newsletter, record a fun video, and conduct hands-on training sessions to catch attention in various ways.
- Make it fun!
-
For more information on personality types in change management, check out our blog: “Embracing the Creature of Habit.”
AUDIT & METRICS
The HGTV Approach to Rehabbing Your IG/RIM Program
Kiersten McAvoy, Principal Consultant – Information Governance, Ricoh-USA
Kedar Thakkar, Principal Consultant – Information Governance, Ricoh-USA
One of the most important characteristics of Access Sciences’ Governance Model is that it’s a continuous process. It doesn’t just stop after a system implementation or initial training. Step 7: Audit & Metrics is about continuing to monitor, evaluate, and improve your IG program.
Kiersten McAvoy and Kedar Thakkar touch on this idea with their presentation, comparing home renovations on HGTV to IG program renovations.
The drivers behind a renovation are similar for both:
-
-
- An unorganized, untidy chaos of items (or information)
- An increase in family size (or volume of information)
- Damage, wear, and tear (or breach, data loss, litigation, etc.)
- Changes in innovation and modernization
-
The solutions for renovating are also similar for both:
-
-
- Fix the repairs that need to be made to the house (or information environment)
- Gut and rebuild the house (or build new information-related policies)
- Add staging with new appliances, furniture, décor, etc. (or bring in new tools and technologies)
-
If you need help deciding whether or not you should onboard a third-party partner, check out our blogs:
For both types of renovations, Kiersten and Kedar suggest understanding the actual scope of work beforehand – the budget, timeline to completion, choice of contractor versus in-house activities, and buy-in from stakeholders (family members or employees).
They explain that renovations are difficult, but doable with a strong framework. Their 4S IG Framework is built on four pillars: Structure, Strategy, Skills, and Systems.
Structure
You’ll want to appoint special committees/councils dedicated to IG, gain involvement from business stakeholders, and designate resources for IG-related activities.
Strategy
They suggest forming a vision that aligns with the organization’s mission, gaining executive support and sponsorship, as well as determining priorities of short-term and long-term initiatives.
Skills
They recommend certifying your resources, rolling out education and training programs, and continuing to engage business stakeholders.
Systems
You’ll want to assess your IG-related applications, your IT infrastructure, and your manual versus automated business processes.
Using this approach, Kiersten and Kedar advocate building credibility through small achievable targets to make progress in your IG program renovation.
Last week, the Access Sciences team attended ARMA InfoCon 2021 to connect with and learn from other information governance (IG) experts. While we were there, we presented on our own thought leadership and heard a lot of solid advice for building (and sustaining) your IG program.
Following our own 7-Point Governance Model, here are some of our favorite sessions with advice for each stage of your IG program:
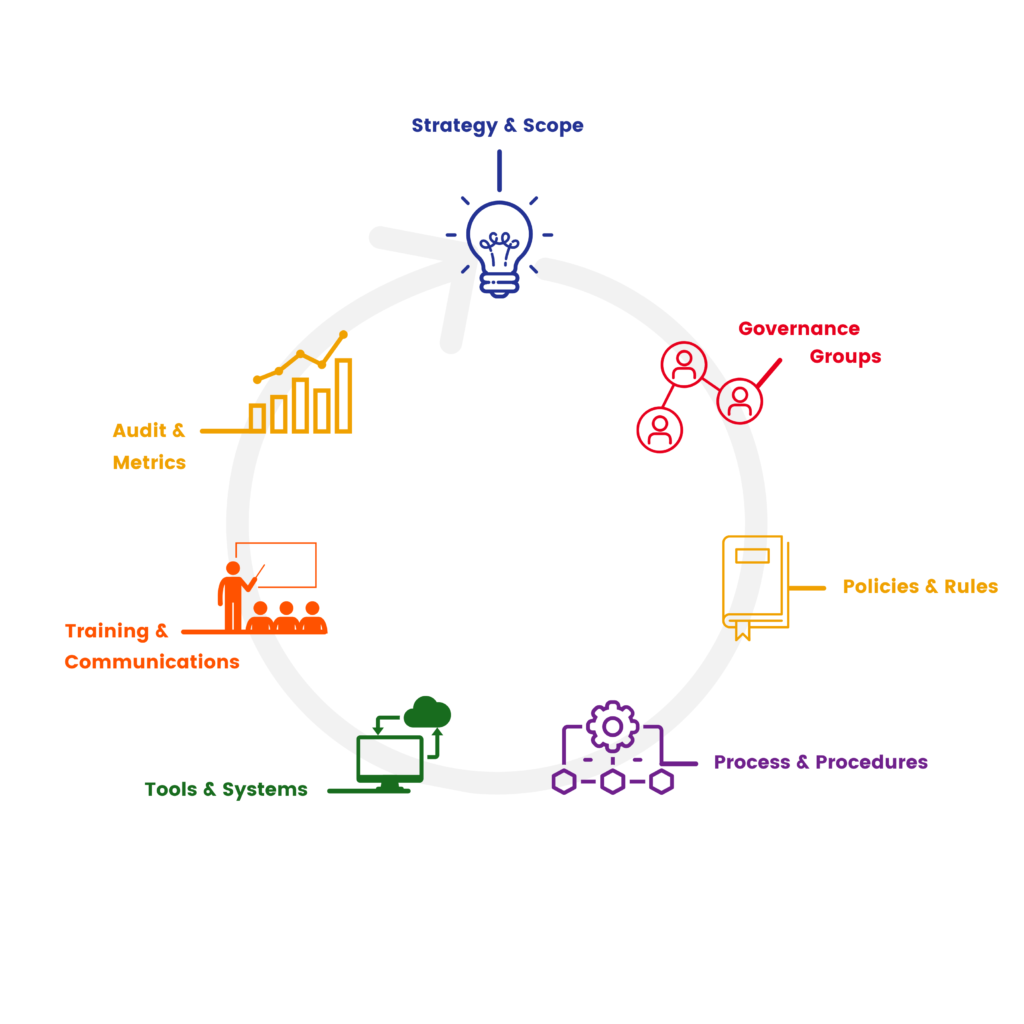
If you missed it, check out our recent blog to learn more about Access Sciences’ 7-Point Governance Model.
STRATEGY & SCOPE
5 Steps to Doing Information Right
Steve Weissman, The Info Guy™, Holly Group
In Step 1: Strategy & Scope, we recommend establishing a vision for your IG program, looking at your available resources, determining your priorities, and focusing on them. Steve Weissman’s ARMA InfoCon session offers advice on how to best execute that with his five steps for building up an IG program.
Step 1: Talk up the benefits.
To start, Steve encourages IG professionals to first answer the question, “Why are we doing this, anyways?” and use that as an opportunity to talk up the benefits of an IG program. He then lists three key benefits to get the conversation started within your organization:
-
-
-
-
- It puts your information to work.
-
Your information is there, so you might as well use it and extract value from it.
-
-
- It opens your information up to analysis and insights.
-
This can shorten your time-to-market, identify opportunities for customer upselling, speed up responses to audit requests, and more.
-
-
-
-
-
-
- It assures your information excellence and security
-
A strong IG program will minimize information security risk by protecting personally identifiable information, ensuring access by authorized users only, and more.
-
-
Step 2: Take Stock (Look Inward)
Similar to our own Governance Model, Steve recommends answering two key questions before embarking on your IG ventures –
-
1. Where are we now?
2. Where do we want to be?
To learn more about IG’s role in information security, check out our blog: “Data Classification for Information Security.”
Step 3: Develop Your Road Map
Once you’ve defined your Point A and Point B, you’ll then want to determine what it’s going to take to get there. To do this, Steve suggests conducting an assessment or gap analysis, which will help you come up with a well-informed game plan towards your desired future state.
For more on assessments, check out our blog: “Assessments: Know What You Don’t Know.”
To remain strategic when determining your priorities, our team advises organizations to conduct a Records & Information Management (RIM) Assessment to “know what you don’t know” from the very beginning.
Step 4: Stay the Course
As with any business feat, you can expect roadblocks ahead. So, commit to the journey!
According to Steve, one of the biggest challenges for IG professionals is getting people on board. That’s why defining the benefits (and communicating them) is essential at the outset of any project.
Step 5: Keep Going (It’s Never Over)
As we like to say at Access Sciences, good governance is never a one-and-done effort. And Steve offers the same exact advice – once your IG program is created, you’ll need to continue analyzing what works and what doesn’t. Then, make changes.
Even after the initial analysis and improvements, Steve recommends conducting a semiannual progress review to make sure your program still fulfills all your information needs.
GOVERNANCE GROUPS
Can’t Get a Seat at the Table? Build Your Own Table!
Earl Johnson, Sr. Records Management Consultant, Cadence Counsel
Step 2: Governance Groups is all about establishing groups across the organization and defining their roles. And we find it’s important that this step starts with gaining executive support.
But what if your organization doesn’t back up your IG initiatives? In his session, Earl Johnson answers that question by describing a time when he (as a Corporate Records Manager) wasn’t invited to the table. So, he made his own.
First, Earl defines what it means to have a seat at the table. He describes “the table” as a symbol of power, negotiation, and credibility which represents the opportunity to be involved in making decisions for your organization.
Then, he offers nine tips to getting a seat at the table:
-
1. Be confident.
2. Be good at what you do – work proficiency is key.
3. Focus on organizational success.
4. Be gravitational – be someone others like being around.
5. Display strong, authentic, and visionary leadership skills.
6. Listen, and check your ego at the door – listen to understand the issues people are facing.
7. Be patient and work through frustration.
8. Play to your strengths.
9. Be an active participant ready with useful contributions.
While these tips are helpful, they don’t guarantee a seat at the table. So, if you’re constantly blocked from the table, you can build your own. Here are Earl’s tips on how to accomplish this:
-
1. Define every aspect of the table – what are you trying to accomplish?
2. Get sponsorship from the executive level.
3. Develop a charter.
4. Identify roles and responsibilities – this will differ from organization to organization, but common groups will include IT, legal, and compliance.
5. Recruit, recruit, recruit.
6. Determine targets – identify what you want to address and why.
7. Be a cohesive team.
His own table, which he called the Records Management Advisory Team (RMAT), was made up of a Corporate Records Manager (Earl), two Subject Matter Experts, the Director of Compliance, the Director of Internal Auditing, the Sr. Manager of Operations, the Director of IT, two IT Senior Managers, the VP and General Counsel, and a Sr. Attorney.
According to Earl, the RMAT was successful because the group had the expertise – the right set of individuals to make decisions for the organizations.
POLICIES & RULES
Impact of Data Protection Laws on Your Records Retention Schedule
Tom Corey, Senior Manager, HBR Consulting
In Step 3, IG professionals establish Policies & Rules that balance the need for privacy and security. While this differs significantly based on your company’s culture and regulatory landscape, we’re all facing the current and/or impending impact of data protection laws.
Tom Corey joined ARMA InfoCon to help IG professionals understand data protection laws’ impact on records retention schedules. To start, he defines the key terms:
-
-
-
-
- Records Retention Schedule: A policy that (1) identifies the types of records created/retained by the organization and (2) defines the retention period for those identified records.
-
-
-
- Data Protection Laws: Laws and regulations that control the collection, storage, and disclosure of individuals’ personal and sensitive information.
-
-
-
According to Tom, the biggest complaint with data privacy laws is that there are so many, and they’re constantly changing. However, he says it’s important to note that these laws are more similar than you think.
Tom explains all data privacy laws and regulations surround Personal Identifiable Information (PII) and retention periods, meaning PII is kept only as long as necessary to fulfill the stated purpose. And to help, he provides four fundamental tools to ensure you stay in compliance with data privacy laws:
-
1. Retention schedule for all media types
Your retention schedule should reflect your current organization as well as jurisdictions where you operate. It should also reflect the systems in use and be applicable to both paper and electronic records.2. Identify categories with PII
Tom advises IG professionals to identify marketing and customer information, employee personnel files and job applications, as well as security footage and access information.3. Justify retention period for those categories
According to Tom, you can justify a retention period with (1) laws and regulations regarding minimum/maximum retention time, (2) a legitimate business purpose (like a contract), or (3) informed consent of the data subject.4. Add records categories that address data protection laws
Lastly, Tom suggests adding records categories that go along with data protection laws like breach notifications, consumer consents, data subject requests/responses, or privacy policies and procedures.
PROCESS & PROCEDURES
The Real Deal with Autoclassification: Can It Really Be Automatic?
Tom Preece, Director of Pre-Sales Consultancy, North America Rational Enterprise
In Step 4, our experts recommend taking your Policies & Rules and turning them into Processes & Procedures for your organization. In his ARMA InfoCon session, Tom Preece touches on a part of this step by covering auto classification.
With ARMA’s own definition, Tom defined it as “leveraging technologies to automatically analyze information and apply transformation” which can mean –
-
-
-
-
- Relocating files
- Adding/removing metadata
- Adding/removing categorization
- Adding/removing policy
- Adding/removing permissions
- Starting a workflow
-
-
-
Or “transformation” can mean a combination of all of the above.
Regardless of what you’re trying to do with auto classification, Tom points out that it can’t be leveraged until you define the “if ___, then ___.” For example, if a file reaches the end of its retention period, then it gets deleted.
Before adopting auto classification, Tom recommends asking yourself:
-
-
-
-
- What scope of my information can auto classification actually apply to?
- How segmented is my organization? What are their different levels of compliance?
- What are the different formats of my organization’s information?
- What is the quantity of my organization’s information?
- Where is my information?
- How much does it cost me to manually perform the transformation I’m looking to automate?
- What is the cost to implement the technology? Not just quantitative but also qualitative – for example, a negative cultural attitude towards automation.
-
-
-
Answers to these questions should be known before making any purchasing decision. Then, you’ll need to determine which approach is right for you – auto-taxonomy, key-value extraction, machine learning? For each of these, you’ll want to prove that it can not only work for day-to-day operations, but that it will also work under the most challenging circumstances your organization faces.
TOOLS & SYSTEMS
Streamline Access to Public Records with a Modern EDMS
Glenn Frederickson, Records Management Project Manager, Access Sciences
Tina Gibeson, Senior Records Analyst, Access Sciences
Step 5 is all about choosing Tools & Systems that will support different parts of your data lifecycle. Access Sciences’ experts, Tina Gibeson and Glenn Frederickson, joined ARMA InfoCon to talk about upgrading one of the Louisiana Department of Environmental Quality’s mission-critical systems – its Electronic Document Management System (EDMS).
To learn more about LDEQ’s EDMS Redesign, check out our case study and podcast episode for the story behind the project.
Traditionally, the public had to go to LDEQ in-person to access records which were stored in file rooms. Then, in 2004, LDEQ hired Access Sciences to develop a public records database that would –
-
-
-
-
- Take the records-retrieval burden off LDEQ employees and staff.
- Improve the publics records-retrieval experience.
- Improve information governance.
- Improve legal and compliance.
- Reduce costs.
-
-
-
LDEQ’s EDMS officially rolled out in 2006 and has since grown to hold more than 7.25 million documents, host about 5,000 users per month, see about 170,000 page views per month, and experience regional, national, and international access.
However, after 15 years, LDEQ realized its EDMS was starting to show its age. So, LDEQ (along with its now long-term partner, Access Sciences) moved to incorporate new, modern features in five different categories:
-
1. User Experience
– Updated UI to match LDEQ website design
– Improved process screens to be more intuitive
– Added enhanced visuals2. Customization & Preferences
– Added an EDMS user account capability for LDEQ staff and public users
– Added a “saved searches” feature
– Added email alert notifications for saved searches3. Search Enhancements
– Refined searches using faceted-search filters
– Separated quick and advanced search
– Dynamically changed the search layout screen
– Added a toggle between two display types4. User Authentication
– Built three user levels – LDEQ employee, registered public user, and guest
– Assigned roles and privileges by level5. Access Restriction and Security
– Assigned tiered document access protection based on user roles – Access Right 1: Public/LDEQ, Access Right 2: LDEQ, and Access Right 5: Authorized LDEQ Only
– Incorporated Captcha for document access
Tina and Glenn’s presentation showed how one system upgrade can change an entire organization, increasing business value significantly. The team uses Google Analytics to track how the EDMS is being used, and the results from the redesign are already proving to justify the cost of the overall records management contract and program.
TRAINING & COMMUNICATIONS
Gaining Buy-In for Your IG Program
Susan Gleason, Information Governance Manager, Shipman & Goodwin LLP
In Step 6: Training & Engagement, we encourage IG professionals to inspire a data-driven culture by training early and communicating often. When it comes to an information-related project, implementing a new system isn’t the hard part – the hard part is getting people to change the way they work.
Change management is often one of the biggest IG roadblocks. That’s why Susan Gleason used her session to offer advice on how to gain buy-in for your IG program. Here are her tips:
-
-
-
-
- Always have your elevator speech prepared.
Susan’s first piece of advice to is to prepare an elevator speech for your IG program that is backed by a clear and achievable vision. It should be applicable across the organization, meeting the entire team’s needs – not just yours.
- Always have your elevator speech prepared.
-
-
-
-
-
-
-
- Know your people. Earn their trust.
You should gain an understanding of what people do, how they work, and what they need. Take into consideration different personality types (which Susan describes as the Pioneers, the Guardians, the Drivers, and the Integrators) and what it takes to get each onto your side. Some are more logic-driven (drivers) while some are more relationship-driven (integrators).
- Know your people. Earn their trust.
-
-
-
For more information on personality types in change management, check out our blog: “Embracing the Creature of Habit.”
-
-
-
-
- Follow the KISS Principle.
According to Susan, KISS stands for Keep It Short and Simple. If an IG policy is 30+ pages, make a short, one-page how-to guide for your colleagues. They’ll appreciate the summarized version much more than the original.
- Follow the KISS Principle.
-
-
-
-
-
-
-
- Clarify the reward.
It’s important to communicate the benefits often. What is the organization gaining? What is their specific department or team gaining?
- Clarify the reward.
-
-
-
-
-
-
-
- Make it fun!
Our team likes to use several training and communications methods to reach our different audiences. Send out an information newsletter, record a fun video, and conduct hands-on training sessions to catch attention in various ways.
- Make it fun!
-
-
-
AUDIT & METRICS
The HGTV Approach to Rehabbing Your IG/RIM Program
Kiersten McAvoy, Principal Consultant – Information Governance, Ricoh-USA
Kedar Thakkar, Principal Consultant – Information Governance, Ricoh-USA
One of the most important characteristics of Access Sciences’ Governance Model is that it’s a continuous process. It doesn’t just stop after a system implementation or initial training. Step 7: Audit & Metrics is about continuing to monitor, evaluate, and improve your IG program.
Kiersten McAvoy and Kedar Thakkar touch on this idea with their presentation, comparing home renovations on HGTV to IG program renovations.
The drivers behind a renovation are similar for both:
-
-
-
-
- An unorganized, untidy chaos of items (or information)
- An increase in family size (or volume of information)
- Damage, wear, and tear (or breach, data loss, litigation, etc.)
- Changes in innovation and modernization
-
-
-
The solutions for renovating are also similar for both:
-
-
-
-
- Fix the repairs that need to be made to the house (or information environment)
- Gut and rebuild the house (or build new information-related policies)
- Add staging with new appliances, furniture, décor, etc. (or bring in new tools and technologies)
-
-
-
For both types of renovations, Kiersten and Kedar suggest understanding the actual scope of work beforehand – the budget, timeline to completion, choice of contractor versus in-house activities, and buy-in from stakeholders (family members or employees).
They explain that renovations are difficult, but doable with a strong framework. Their 4S IG Framework is built on four pillars: Structure, Strategy, Skills, and Systems.
Structure
You’ll want to appoint special committees/councils dedicated to IG, gain involvement from business stakeholders, and designate resources for IG-related activities.
Strategy
They suggest forming a vision that aligns with the organization’s mission, gaining executive support and sponsorship, as well as determining priorities of short-term and long-term initiatives.
If you need help deciding whether or not you should onboard a third-party partner, check out our blogs:
Skills
They recommend certifying your resources, rolling out education and training programs, and continuing to engage business stakeholders.
Systems
You’ll want to assess your IG-related applications, your IT infrastructure, and your manual versus automated business processes.
Using this approach, Kiersten and Kedar advocate building credibility through small achievable targets to make progress in your IG program renovation.
ADDITIONAL INFORMATION
For more IG thought leadership, check out the rest of Access Sciences’ expert-driven content!